In cybersecurity, log management plays a critical role in identifying security threats, troubleshooting system issues, and ensuring compliance with industry regulations. Every action taken within a network generates logs, from user logins to software updates, security breaches, and failed authentication attempts. Managing these logs effectively allows organizations to detect and respond to cyber threats in real time.
This article provides a detailed, step-by-step guide on log management in cybersecurity, covering its importance, best practices, tools, and implementation strategies. Whether you’re an IT professional, security analyst, or business owner, this guide will help you understand how to protect your digital assets through proper log management.
What is Log Management?
Gathering system, application, and network device log data involves collection, storage, analysis, and monitoring activities. Through this data, an organization gains fundamental knowledge about its security posture.
Log management key components involves:
- Log Collection – Gathering log data from different sources (servers, applications, firewalls, etc.)
- Log Storage – Storing logs securely for future analysis and compliance
- Log Analysis – Analyzing logs for patterns, anomalies, and threats
- Log Monitoring – Real-time tracking of events to detect security incidents
- Log Retention – Keeping logs for compliance and forensic investigations
Types of Logs Generated by IT Systems:
IT systems create log files that document program activities taking place inside the system. The information stored in logs provides considerable value for both fixing system issues and security investigation and compliance record keeping. The main categories of logs involve:
- System logs: Generated by operating systems, tracking system events and errors.
- Application logs: Created by software applications to log activities and errors.
- Network logs: Captured by firewalls, routers, and switches to track network traffic.
- Security logs: Recorded by security tools like antivirus software, intrusion detection systems (IDS), and firewalls.
- Audit logs: Contain records of user activities, access permissions, and administrative actions.
Sources of Log Data:
The organizational log data originates from different operational points which include:
- Servers and endpoints
- Firewalls and intrusion detection systems
- Cloud services and applications
- Identity and access management (IAM) solutions
Why is Log Management Important in Cybersecurity?
1.Threat Detection & Incident Response:
Organizations use log data as a tool to detect suspicious behaviors as well as unauthorized system access attempts and possible malware attacks. Log analysis tools enable security teams to discover irregularities along with enabling quick response against security threats.
2. Regulatory Compliance:
Business sectors under GDPR, HIPAA, PCI-DSS and SOC 2 regulations must maintain and assess log data for their security assessment needs.
3. Forensic Investigations:
The incident investigation benefits from forensic experts through digital evidence contained in log files to reveal breach details like attack methods and responsible parties in cases of cyberattacks.
4. Performance & Troubleshooting:
System logs have dual purposes in addition to security functions since they help users detect operational breakdowns and repair software problems and enhance system efficiency.
Step-by-Step Guide to Log Management
The following steps of log management are:
Step 1: Identify Log Sources:
The process begins by establishing which systems together with network devices along with applications create logs. Common log sources include:
- Windows Event Logs and Linux Syslogs serves as log sources among other operating systems.
- This category includes the group of network devices that includes firewalls, additional Routers, and IDS/IPS functions.
- The set includes Web servers together with Databases and Cloud Services.
- Security Tools (SIEM, Antivirus, EDR)
The best practice mandates that important system settings should be configured to create logs because security gaps develop from absent data logs.
Step 2: Define Log Management Policies:
Create guidelines that identify the log data assortment as well as define both storage duration along with access control systems for security purposes and regulatory compliance needs.
- Define Log Retention Periods: The definition of log retention duration needs precise definition according to specific regulatory requirements where PCI-DSS demands one year of log storage as an example.
- Determine Log Access Controls: The access policy must identify which personnel needs to see log data because unauthorized viewing should be prevented.
- Classify Log Data: Workers should prioritize vital security logs over secondary logging data because different security messages hold different levels of importance.
Step 3: Centralized Log Collection & Storage
Multiple devices require inefficient manual inspection of logs. Log management should be built using centralized aggregation systems to collect information from each source into a unified location.
- On-Premise Log Management Tools: Organizations having total log management authority and demanding complete control should use Splunk and Elastic Stack as on-premises solutions.
- Cloud-Based Log Management Solutions: Scalable and managed solutions for businesses of all sizes. (e.g., AWS CloudTrail, Datadog)
Log encryption serves as an optimal practice to establish secure storage by defending against unauthorized manipulation and unauthorized access to data.
Step 4: Log Parsing & Normalization
System log outputs exist in different formats which creates challenges for smooth analysis processing. An analysis-friendly standardized format emerges from log normalization processes that normalize various log formats.
- Log parsers should be implemented to extract fundamental data points which include user IDs together with IP addresses and timestamps.
- Organizations should operate structured logging formats including JSON, XML and Common Event Format (CEF).
The best practice for real-time log normalization involves using automated tools which include Logstash or Fluentd.
Step 5: Real-Time Log Monitoring & Alerting
Predominant organizations need to run nonstop log monitoring alongside suspicious activity alert systems to prevent cyber threats.
- SIEM tools should be implemented to perform automated security monitoring functions.
- Real-time alerts for failed logins unauthorized access as well as malware detection should be established.
- The implementation of behavioral analytics should be used to monitor for non-standard activities.
Every organization should deploy machine learning algorithms which detect security risks during their initial stages.
Step 6: Log Analysis & Correlation
The analysis phase begins after collecting the logs to identify security incidents.
- The correlation of events between different log sources can be achieved through utilization of SIEM tools like Splunk, Graylog or IBM QRadar.
- Organizations should implement Threat Intelligence Feeds to recognize both known malicious IPs along with threatening behaviors.
- An organization must carry out post-security breach forensic log investigation to discover the source of attacks.
SIEM rules must be subjected to regular audits for rule adjustments to minimize false alarm occurrences.
Step 7: Log Retention & Compliance
Log storage duration plays an essential role because organizations depend on it both for complying with regulations and for investigation needs.
- The healthcare industry requires businesses to retain logs for at least six years according to HIPAA regulations.
- Organizations should develop storage methods which securely maintain historical log records.
- You should perform scheduled audits of your log storage areas to verify both integrity and operational availability.
The best approach for log protection includes immutable storage which stops anyone from modifying logs.
Working of Log Management in Cybersecurity
Security-driven log management operates through systematic steps which allow organizations to acquire log data and analyze this data and store it as well as monitor its progress. Log management performs this process through the following sequence which I will explain below.
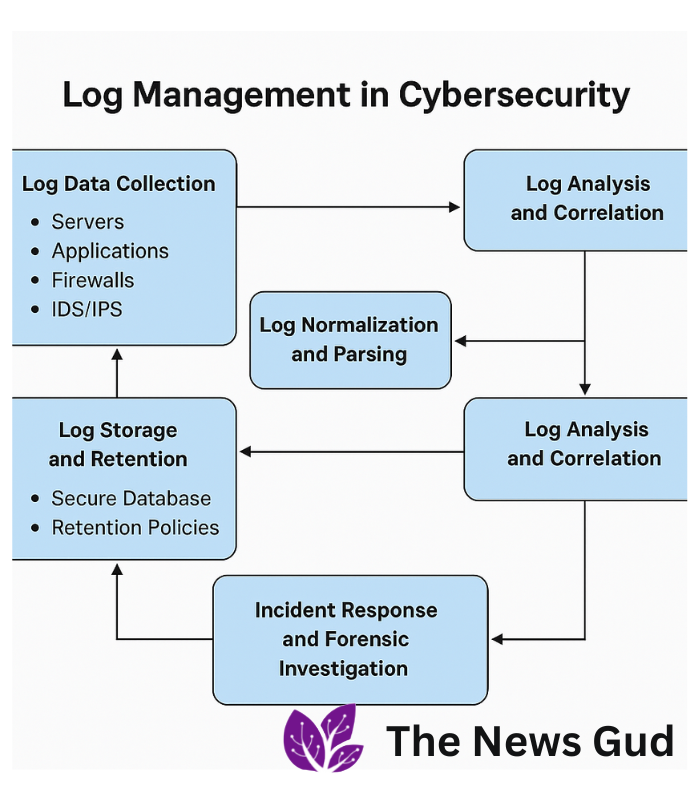
1. Log Data Collection:
- Numerous platforms supply logs through servers along with applications as well as firewalls and IDS/IPS products along with cloud-based services and endpoint system outputs.
- The central logging system receives log data from agents and collectors which are installed by log management tools.
2. Log Normalization and Parsing:
- Normalization transforms log records from various formats into an uniform standard so the data becomes easier to process.
- The log parsing process separates various information types from raw data logs to generate timestamp fields as well as user actions and event type and IP address details.
3. Log Storage and Retention:
- Secure databases as well as cloud storage serve as storage systems for logs which protect them from tampering through encryption.
- Organizations create log storage rules through their compliance needs together with their own information defense standards.
4. Log Analysis and Correlation:
- Analysis of security logs by teams enables detection of both abnormal system events and unwanted access attempts and system breakages and security attacks.
- Security teams use log correlation to understand patterns within large amounts of entries which reveals how attackers perform brute-force attacks as well as malware infiltration activities.
5. Real-Time Monitoring and Alerting:
- Real-time security anomaly detection happens through active log management systems.
- The system generates automatic notification alerts after discovering unusual user activity which involves repeated unsuccessful login tries.
6. Incident Response and Forensic Investigation:
- A security breach produces vital forensic evidence available through logs that helps security teams track where the attack originated from together with identifying which systems got affected and examining the extent of data loss.
- Security teams depend on log analysis reports to take prompt action and minimize threats in order to enhance upcoming defense measures.
Challenges in Log Management
The establishment of effective log management strategies for cybersecurity encounters multiple implementation hurdles by organizations.
1. High Volume of Logs:
- Enterprise-level organizations need to handle thousands of millions of daily logs which creates challenges for data storage management along with efficient analysis.
- Excessive data leads to security team overwhelm when automated log processing is absent from their process.
2. Identifying False Positives and False Negatives
- Alert fatigue occurs when security teams face numerous alarms that include fake threats among real ones.
- Organizations become insecure to cyberattacks because insufficient log correlation fails to detect important threats therefore producing false negative results.
3. Storage and Retention Issues:
- Managing log storage systems for compliance purposes becomes more costly because authentication regulations require organizations to retain records for specific time periods (PCI-DSS prescribes one year).
- Efficient storage solutions are needed by organizations to provide secure and tamper-proof accessibility for log data storage.
4. Log Data Privacy and Security:
- Logs hold multiple types of sensitive data ranging from user account information to passwords together with customer related information.
- The protection of logs from tampering and data breaches requires organizations to establish encryption systems together with access controls and anonymous data methods.
5. Lack of Skilled Personnel:
- Successful log management demands people who can analyze data, understand threats and conduct forensic investigations.
- An insufficient number of cybersecurity experts creates a widespread problem for organizations attempting to perform complete log analysis and incident response.
6. Integration with Existing Security Infrastructure:
- Security log management solutions need to deliver end-to-end connectivity with all forms of information security technology including SIEM as well as endpoint security products firewalls cloud-based environments and external third-party security systems.
- Security information becomes less effective due to incompatibility problems between different systems which creates data silos.
7. Compliance and Legal Challenges:
- Log management creates problems for organizations because different businesses need to follow separate sets of regulations such as GDPR and HIPAA as well as PCI-DSS and SOX.
- Required legal compliance standards require every breach of laws to result in fines as well as potential lawsuits and negative consequences to reputation.
8. Performance and Latency Issues:
- Analyzing real-time log data requires systems with exceptional computing power capabilities to handle massive information volumes.
- Poorly optimized log management systems can cause delays in threat detection, impacting incident response times.
How to Overcome Log Management Challenges
To address these challenges, organizations can:
- Use AI and machine learning to filter out false positives and detect advanced threats.
- Adopt cloud-based log management solutions for scalable and cost-effective storage.
- Implement strong access controls and encryption to protect sensitive log data.
- Train cybersecurity teams to effectively analyze and respond to security incidents.
- Choose a log management tool that integrates with SIEM for automated security insights.
- Regularly audit and optimize log retention policies to meet compliance requirements.
Conclusion
Log management is an essential cybersecurity practice that helps organizations detect threats, investigate incidents, ensure compliance, and improve security operations. By implementing centralized logging, real-time monitoring, AI-driven analysis, and compliance automation, businesses can stay ahead of cyber threats and reduce risks.
As cyberattacks become more sophisticated, investing in advanced log management tools and following best practices will be key to strengthening security postures and maintaining regulatory compliance.

